Abstract :
This article is providing information about OWASP (Open Web Application Security Project). It will explain the importance of OWASP in current era. We will discuss about Web application attacks, OWASP Top Ten vulnerabilities and OWASP ZAP.
Introduction :
OWASP(Open Web Application Security Project) is useful in enhancing the security of the software. In the organization, the development team is involved in developing the application and security team gives their best to secure that application. While developing the application, the development team should take care of writing the security code as it is expected by the security team and later security team uses some tools(OWASP) to check whether the application is secure or not. When the security team provide the vulnerability assessment report to the developers, it should be specific or in context of the developers’ language that where is the issue and what needs to be changed, instead of writing in layman language.
Security Misconceptions :
Some of the organizations think that SSL(Secure Sockets Layer) and Data encryptions are enough to secure the application. SSL does end to end encryption but it can’t differentiate between the malicious data and the legitimate data. Hence, the SSL is not that helpful in securing the application. Firewalls are also not enough for securing the web application because they expose web applications and servers to the users through the PORT 80 and 443, which are restricted. So it doesn’t scan the data and differentiates between the malicious data and the legitimate data. SSL and Firewall cannot secure the application at the utmost level. Therefore, most of the attacks occur on web applications.
10 Basic Security Checks:
OWASP TOP 10 vulnerabilities come in picture for conducting the vulnerability assessments for web applications. Below is the chart of OWASP TOP 10 vulnerabilities:
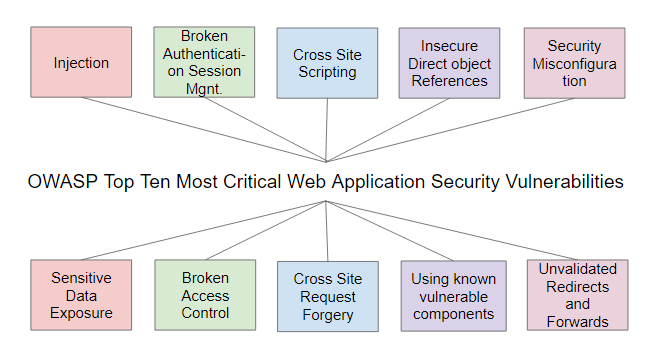
Injection: Injection as the name indicates that “an instance of injecting or being injected” means injecting the malicious script or malicious code to the web application so it gives output in abnormal way.
Basically, if we talk about an example, the SQL injection is a very common example of it. In this injection, the attacker injects the SQL query in the form field of the web application to get the confidential data of the application.
Broken Authentication on Session Management :
Broken authentication means when user login to any website so his/her credentials are protected when hoarded. This kind of feebleness allows the attacker to bypass the authentication methods which is used by the web application. When confidential and important credentials are not sent in encrypted format over the connections then this occurs.
Session ID should be rotated after the successful login of the users. When session timeout is not managed, the user logged in credentials exists on the server for a long time and attackers misuse it. This way, they can steal the user’s credentials so later on, they misuse the user privileges.
Cross-Site Scripting :
Cross-site scripting occurs due to a lack of proper context-specific encoding of the user’s data in the page. It allows the attacker to steal information of user’s session and then performing the actions from their behalf.
Cross-Site Scripting attack occurs when a user enters the data in web application through the non-trustable source and entered data includes the malicious content or entered without validating it.
Insecure Direct object References :
When developer leaves the reference unprotected to the internal implementation object like file or directory without using validation so it helps attackers to access the unauthorized data.
Security Misconfiguration
Security misconfiguration occurs due to insecure configuration. When the poor configuration is made. then attackers can attack at any stage of the application stack. May be attackers guess anything from the error message if they are improperly handled, which could also be an issue related to security.
Sensitive Data Exposure :
Sensitive Data Exposure means any data like credit card numbers, debit card numbers, User account/passwords is exposed or can be decrypt by the attacker. This could be the harmful loss in term of financial loss.
Broken Access Control :
As the name says broken access control means, it is related to authority that when one user can access the content of an application after login and others cannot. These are all related to security checks and authorization that only authorized users are allowed to access it. If this check breaks then the security of an application fails.
Cross-Site Request Forgery :
In the cross-site request forgery, attackers create a malicious request and embed it with the forged hyperlink. After this, they embed this hyperlink to the valid customer request. The forged hyperlink replace the user personal details with the attacker details. So, as soon as the transaction commits, funds goes to the attacker account instead of user account.
Using known vulnerable components :
For designing a project several open libraries and components are used by application. If these open source components were not regularly updated then it will lead to vulnerability.
Unvalidated Redirects and Forwards :
When a web application accepts untrusted input that could cause the web application to redirect the request to a URL. Later on, the attacker modifies this URL into a malicious site to launch a phishing scam and can steal user credentials.
How to use OWASP ZAP:
Install tool form https://www.zaproxy.org/ and start with attack on a testing website to see the security checks:
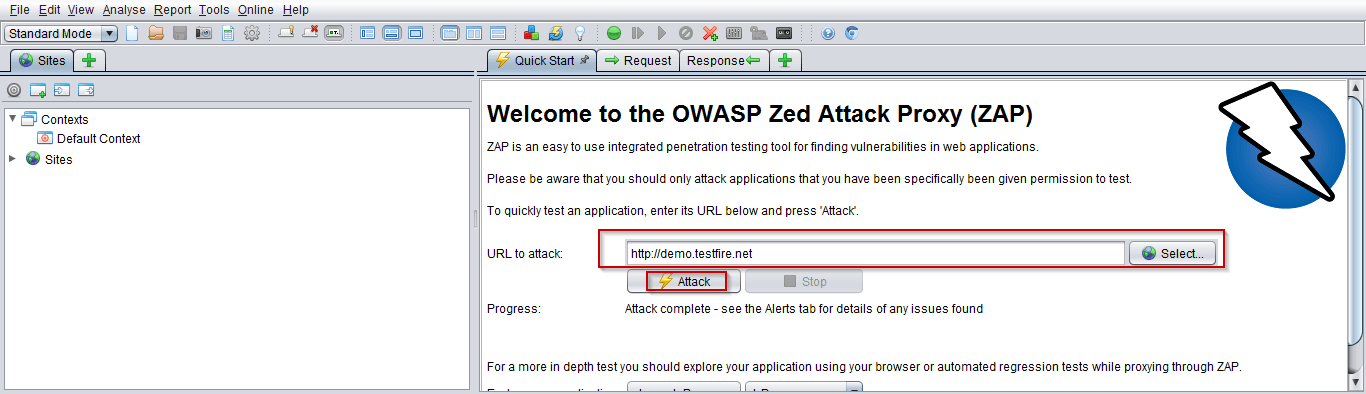
Response after attacking on a website are mentioned below and the good thing about OWASP ZAP it shows the URL in the response that where are the issues.
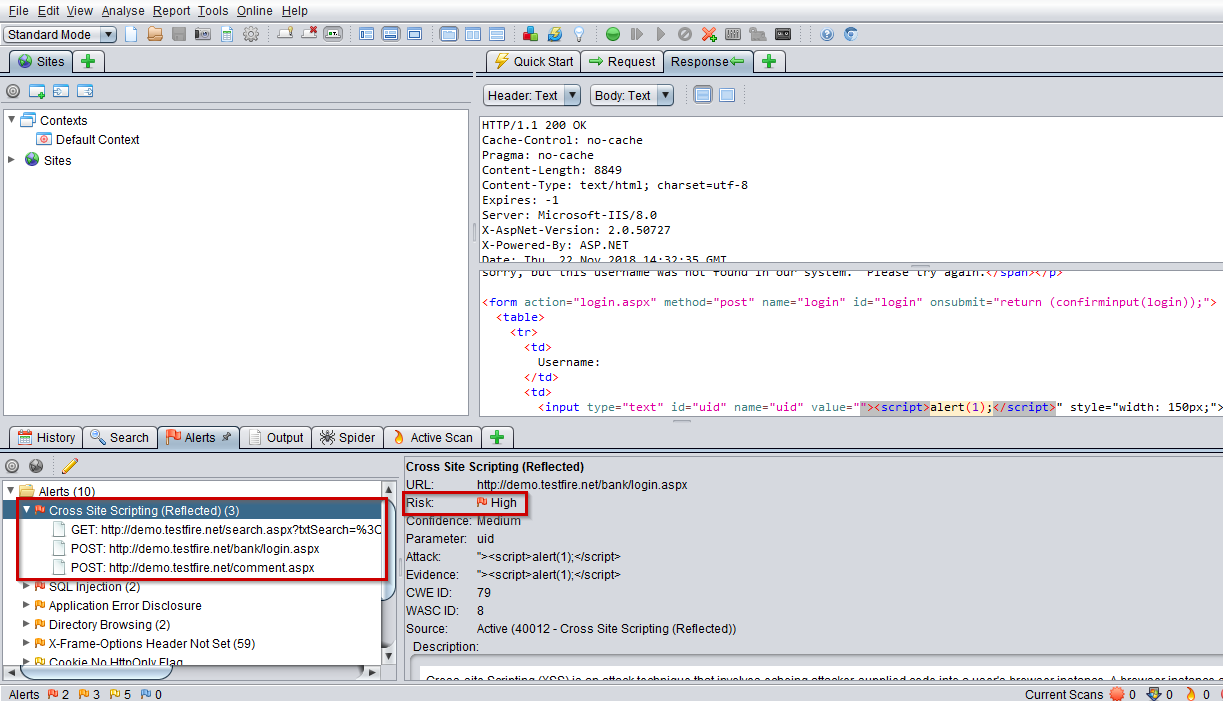
Cross-Site scripting :
Vulnerabilities that exists in cross-site scripting
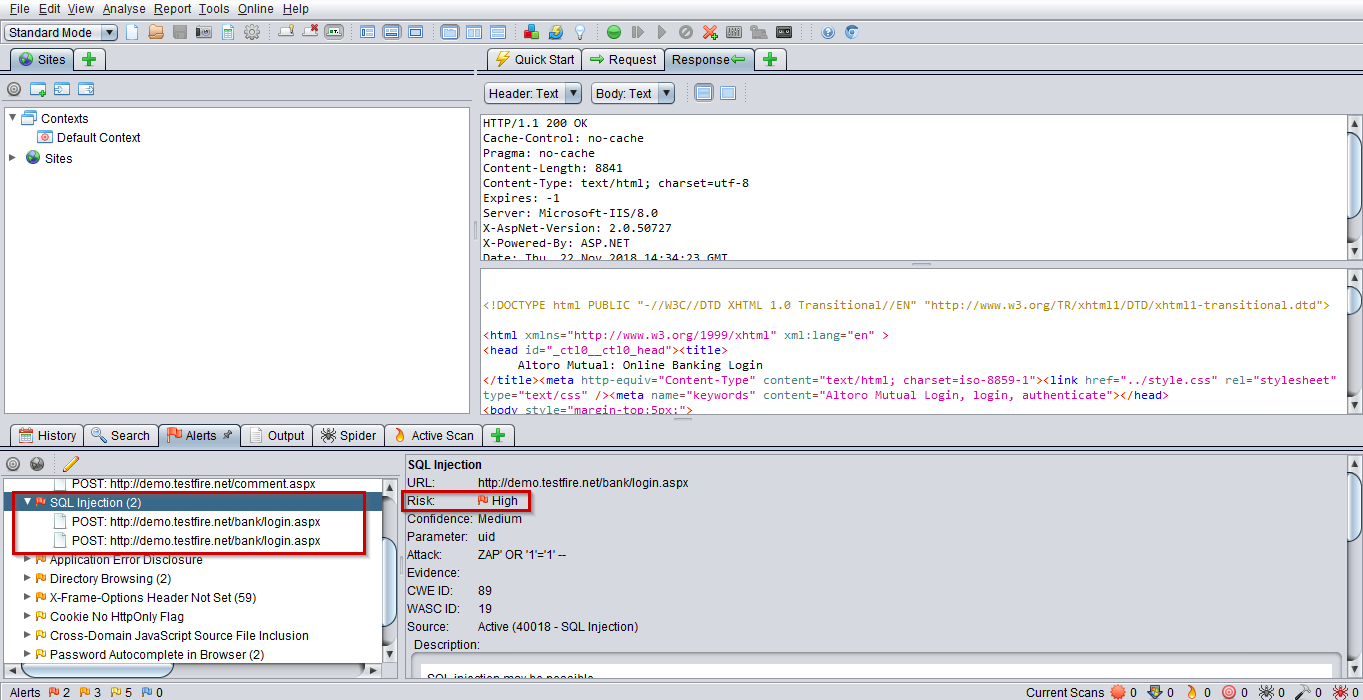
SQL Injection :
Vulnerabilities that exists in SQL injection
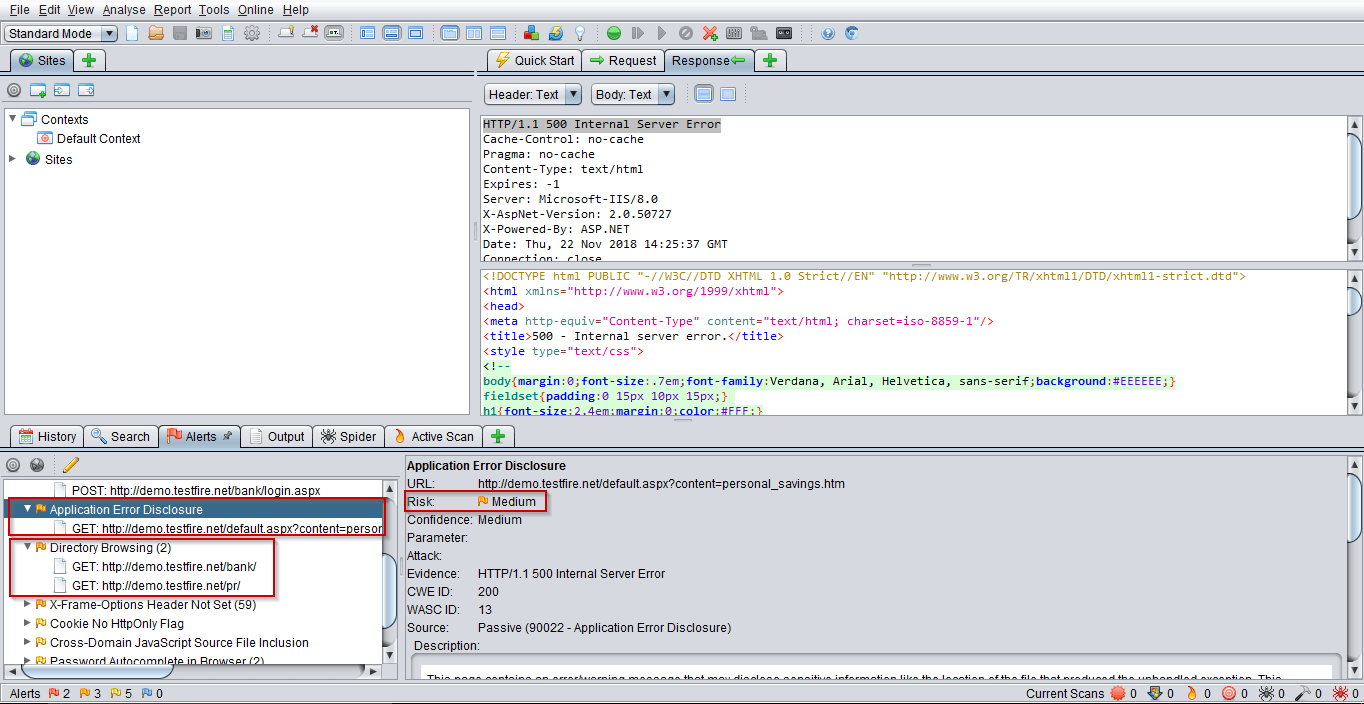
Application Error Disclosure and Directory Browsing :
Vulnerabilities that exists in Application Error Disclosure and Directory Browsing
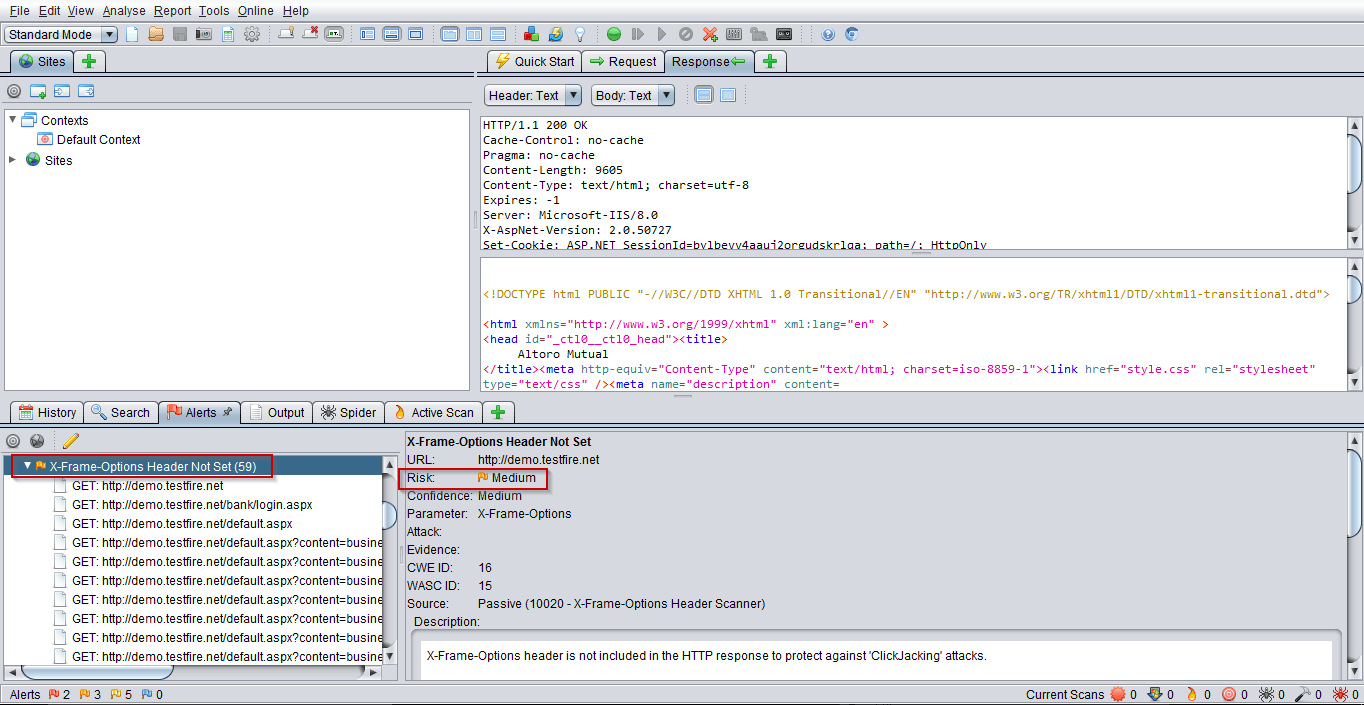
X-Frame options header not set :
Vulnerabilities that exists when X-Frame options headers are not set
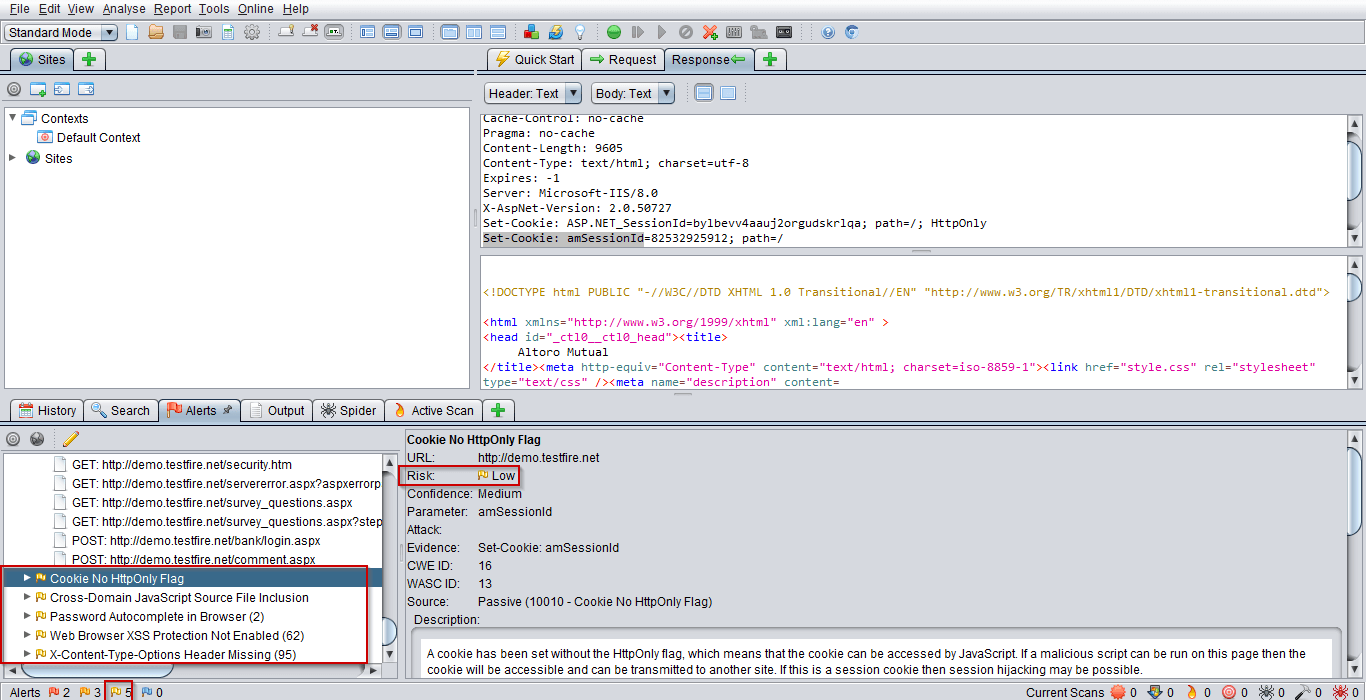
Here we can see some Low Risks area:
About Author:
Priyanka jain is a QA Engineer currently working with QSS Technosoft Pvt Ltd. She is a technology writer in Selenium, SQL and frameworks like TestNG, ReportNG. She has holds her B.tech in Electronics and Communication.
About QSS:
QSS has a proven track executing enterprise level web and mobile applications for itsesteemed customers. QSS has a test center of excellence with a dedicated andexperienced team of QA engineers. To Know More...





