Do you feel sure about the safety of your organization’s dat͏a and systems against cyber threats?͏ I͏f not, we can assist. Do you know that According to the latest survey by Cybersecurity Ventures, worldwide cybercrime prices are expected to attain $10.5 trillion yearly through 2025, up from $3 trillion in 2015? (Shocking right?). This alarming increase highlights the urgency for companies to ͏enhance their cy͏bersecurity de͏fenses. Undergoing VAPT Testing is thus crucial for organizations.
Don’t worry!͏ Vulnerability Assessment and Penetration Tes͏ti͏ng (VAPT) is a top strategy for improvi͏ng security via thorough eva͏luations of networks, systems, ͏and͏ software for potential weaknesses att͏ack͏ers could exploit.
Let us give you a quick example, let’s consider the financial sector. A bank decides to conduct VAPT on their online banking platform. During the assessment, the penetration testers discover a vulnerability in the login mechanism that could allow unauthorized access to customer accounts.
By addressing this vulnerability promptly, the bank mitigates the risk of potential data breaches, financial loss, and reputational damage.
In this blog, we will explore the best practices for conducting VAPT testing and ensuring robust security measures.
Read Also: Uncover the 15 Best Testing Practices for Salesforce App Development
What is VAPT Testing?
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security testing methodology that helps identify vulnerabilities and assess the security posture of software systems, networks, web applications, and IT infrastructure. VAPT testing involves two key processes: vulnerability assessment and penetration testing.
During the vulnerability assessment phase, automated tools are used to scan the target system for known vulnerabilities, misconfigurations, and weak security controls. This phase provides a comprehensive report on the identified vulnerabilities along with severity ratings and recommended fixes.
In the subsequent penetration testing phase, security experts simulate real-world attack scenarios to exploit the identified vulnerabilities and gain unauthorized access to the system. By demonstrating the impact of these vulnerabilities, organizations can understand the potential risks and prioritize their remediation efforts.
For example, consider an e-commerce website undergoing VAPT testing. The vulnerability assessment might uncover a cross-site scripting (XSS) vulnerability in the web application’s user input fields. In the penetration testing phase, a security expert could craft malicious input to exploit this vulnerability and inject malicious JavaScript code into the website. This would highlight the need for input sanitization and output encoding to prevent XSS attacks.
Best Practices for Conducting VAPT Testing
Without following established best practices, VAPT testing can be inefficient and fail to provide accurate results. Let’s discuss the best practices for conducting VAPT testing to maximize its effectiveness.
1. Planning and Goal Setting
Effective VAPT testing starts with careful planning and goal setting. It is crucial to define the scope, objectives, and timelines of the testing process. This includes identifying which systems, networks, or applications will be tested, the specific vulnerabilities to focus on, and the desired outcomes.
For example, setting a goal to identify and prioritize vulnerabilities in the web application login process within a specified timeframe.
2. Establishing Testing Environment
Creating a testing environment that accurately represents the production environment is critical for the success of VAPT testing. This includes duplicating the target systems, networks, and applications, as well as their configurations, to ensure accurate results. The testing environment should also include relevant security controls and policies to simulate real-world scenarios.
For instance, setting up a virtual environment that mirrors the organization’s production network to assess the impact of a potential security breach.
3. Collaboration with Stakeholders
VAPT testing involves multiple stakeholders, including IT teams, developers, and system administrators. It is essential to involve stakeholders from the beginning to gather their insights and expertise. Collaboration helps in identifying critical assets, potential vulnerabilities, and possible remediation strategies.
An example would be involving the development team to understand the underlying code of a web application and identifying possible security vulnerabilities.
4. Methodology Selection
Choosing the right methodology for VAPT testing is crucial for obtaining accurate results. There are various methodologies available, such as the Open Web Application Security Project (OWASP) Testing Guide, the National Institute of Standards and Technology (NIST) guidelines, and the Penetration Testing Execution Standard (PTES).
For example, selecting the OWASP methodology for assessing the security of a web application based on known vulnerabilities listed in the OWASP Top 10.
5. Comprehensive Test Coverage
To ensure comprehensive test coverage, VAPT testing should encompass multiple dimensions. This includes testing from different perspectives such as network, application, and system-level vulnerabilities. Both automated and manual testing techniques should be employed to identify vulnerabilities that may be missed by automated tools.
An example could be conducting a combination of automated vulnerability scans and manual penetration testing to identify and exploit vulnerabilities in a network infrastructure.
6. Use of Up-to-date Tools and Techniques
VAPT testing relies heavily on tools and techniques to identify vulnerabilities and assess their impact. It is crucial to use up-to-date and reliable tools that align with the latest industry standards. Tools should be regularly updated, and their configurations should be optimized for accurate testing.
For instance, using automated tools such as Nessus or OpenVAS to scan for known vulnerabilities in network devices and web applications.
7. Documentation and Reporting
Accurate and detailed documentation is vital for successful VAPT testing. Testers should record all testing activities, including the testing environment setup, executed tests, identified vulnerabilities, and their impact. Clear and concise reporting is essential to communicate the findings to stakeholders effectively.
An example would be documenting the steps taken to exploit a vulnerability in a system and providing recommendations for mitigation in a detailed report.
Read Also : Guide & Cost to Develop YouTube Like App
8. Remediation and Validation
VAPT testing is not complete without proper remediation and validation of identified vulnerabilities. Organizations should promptly address the identified vulnerabilities and implement appropriate remediation measures. It is crucial to validate the effectiveness of the remediation by retesting the vulnerabilities after applying the fixes.
For example, patching the identified vulnerabilities in a web server and retesting to ensure that the vulnerabilities have been successfully mitigated.
9. Continuous Testing Efforts
VAPT testing is not a one-time activity. Organizations should establish a culture of continuous testing to maintain the security of their systems. Regular testing helps identify new vulnerabilities that may arise due to changes in technology, new threats, or system updates.
An example could be scheduling regular monthly vulnerability scans and penetration tests to proactively identify and remediate new security weaknesses.
10. Compliance with Legal and Ethical Guidelines
Lastly, it is essential to conduct VAPT testing in compliance with legal and ethical guidelines. Organizations should ensure that they are authorized to test the systems and obtain necessary permissions from stakeholders before conducting any testing activities. Tester ethics should be prioritized, and confidentiality, integrity, and professional conduct should be maintained throughout the testing process.
For instance, obtaining written permission from the organization’s legal department before conducting VAPT testing on their internal systems to ensure compliance with legal requirements.
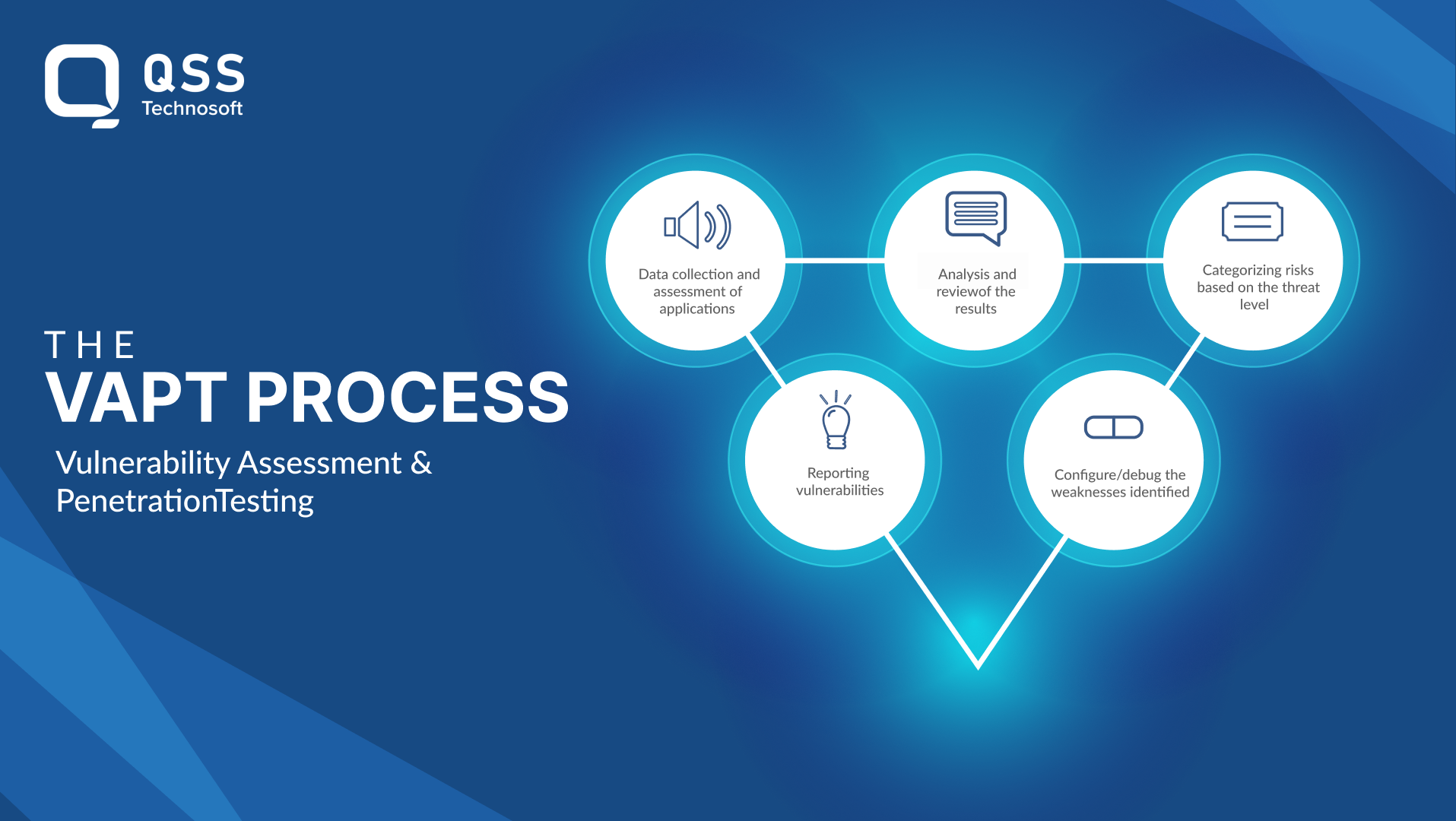
Steps to Conducting Vulnerability Assessment and Penetration Testing (VAPT)
Here are the key steps involved in conducting a VAPT test:
- Step 1: Scope Definition
Define the scope of the VAPT test by identifying the target systems, networks, and applications to be tested. This includes determining the goals, objectives, and constraints of the testing process.
Example: In a web application VAPT test, the scope might include testing the login functionality, data input forms, and session management features.
- Step 2: Vulnerability Assessment
Conduct a thorough vulnerability assessment to identify potential security flaws and weaknesses in the target systems. This involves using automated tools and manual testing techniques to scan for known vulnerabilities, misconfigurations, and other security issues.
Example: Using tools like Nessus or OpenVAS to scan for common vulnerabilities such as SQL injection or cross-site scripting (XSS) in a web application.
- Step 3: Penetration Testing
Perform penetration testing to simulate real-world cyber attacks and exploit the identified vulnerabilities. This step involves attempting to infiltrate the target systems using various techniques, such as social engineering, network scanning, and exploitation.
Example: Using tools like Metasploit to exploit a known vulnerability in a web server to gain unauthorized access.
Read Also : Spotify Clone: A Step-by-Step Guide to Developing Your Music Streaming App
- Step 4: Reporting
Compile a detailed report outlining the findings, vulnerabilities, and recommendations identified during the VAPT test. The report should include a prioritized list of vulnerabilities, potential impact assessments, and remediation steps to mitigate the risks.
Example: Providing recommendations such as patching vulnerable software, implementing secure coding practices, and enhancing network security controls.
Conclusion
VAPT testing is absolutely essential for any organization serious about protecting their valuable assets. By adhering to the best practices mentioned above, companies can stay one step ahead of cyber attackers and ensure their cybersecurity program is robust and effective.
But hey, here’s a little surprise for you – if you think cyber threats are just a piece of cake and you enjoy playing hide and seek with hackers on your own (good luck with that!), Reminder to not to skip VAPT testing.
However, for those smart to recognize the importance of security, it’s time to take action. So, why not partner with a reliable and experienced team like QSS Technosoft for all your VAPT testing needs? Our professional expertise and cutting-edge solutions will give you the peace of mind you deserve. Don’t be a cyber victim – take the first step towards a secure future and contact QSS Technosoft today.
Reach out to QSS Technosoft now and safeguard your organization from cyber threats! Remember, it’s not a one-time activity, but an ongoing process that requires continuous evaluation and improvement.
We are proud to mention that our work has been recognized by leading B2B reviews and research platforms like GoodFirms, Clutch, MirrorView, and many more.