Can you confidently say that your corporation’s virtual assets are stable towards the growing risk? The growing number of cyberattacks and records breaches has made it critical for corporations to prioritize their cybersecurity efforts & go for VAPT Testing.
According to a current take look at by Ponemon Institute, the average cost of a statistics breach in 2020 became $3.86 million. This alarming discern emphasizes the importance of implementing robust safety features to guard sensitive records and infrastructure.
To address those threats proactively, businesses use strategies inclusive of vulnerability assessment and penetration testing. These processes assist in perceiving vulnerabilities in networks, packages, and systems before malicious actors can exploit them.
Take, for instance, an e-trade organization. With patron facts and monetary transactions at stake, it’s vital for them to assess the safety in their online platform often. With customer data and financial transactions at stake, it is imperative for them to assess the security of their online platform regularly. By conducting vulnerability assessments and penetration testing, they can reveal potential weaknesses and strengthen their security posture.
To carry out these assessments effectively, security professionals rely on a comprehensive toolkit of tools and techniques. This toolkit helps identify vulnerabilities, analyze potential risks, and provide valuable insights to enhance overall security.
In this blog post, we will explore some of the top tools available in the market that can assist in conducting these tests efficiently.
Read Also: Uncover the 15 Best Testing Practices for Salesforce App Development
1. Nessus
Nessus is one of the most widely used vulnerability assessment tools. It is known for its comprehensive network scanning capabilities, which can detect vulnerabilities across multiple platforms and devices. Nessus provides detailed reports on the vulnerabilities found, enabling organizations to prioritize and address them promptly. It also offers integration with other security tools and platforms, making it a favorite among security professionals.

Benefits:
- Comprehensive Network Scanning: Nessus offers extensive network scanning capabilities, allowing users to detect vulnerabilities across multiple platforms and devices within their network.
- Detailed Vulnerability Reports: The tool provides detailed reports on the vulnerabilities found, enabling organizations to prioritize and address them promptly.
- Integration with Other Tools: Nessus integrates with various security tools and platforms, making it easy to incorporate into existing security workflows.
- Continuous Updates: Nessus is regularly updated with the latest vulnerability checks, ensuring that users have access to up-to-date information for more accurate assessments.
- Advanced Configuration Auditing: It offers advanced configuration auditing capabilities, helping organizations ensure compliance with industry standards and best practices.
2. Nexpose
Nexpose is another powerful vulnerability assessment tool that provides in-depth scanning capabilities. It can identify vulnerabilities in various systems, including networks, databases, web applications, and more. Nexpose offers real-time monitoring and scoring, allowing organizations to stay updated on the security posture of their infrastructure. Additionally, it provides remediation advice to help teams address the identified vulnerabilities effectively.

Benefits:
- In-Depth Scanning: Nexpose provides in-depth scanning capabilities, enabling users to identify vulnerabilities across various systems, including networks, databases, web applications, and more.
- Real-Time Monitoring and Scoring: The tool offers real-time monitoring features, providing organizations with a continuous view of their security posture and scoring vulnerabilities based on their severity.
- Remediation Advice: Nexpose provides actionable remediation advice, helping organizations address identified vulnerabilities effectively and reduce the risk of exploitation.
- Integration and Automation: It supports integration with other security tools and can be easily incorporated into automated security workflows, saving time and effort for security teams.
- Expansive Features: Nexpose offers a wide range of features, including asset discovery, asset profiling, and risk assessments, making it a comprehensive vulnerability assessment tool.
Read Also: How to Build an App like Trezor Cryptocurrency Wallet?
3. OpenVAS
OpenVAS (Open Vulnerability Assessment System) is an open-source vulnerability scanner. It is known for its versatility, allowing users to conduct comprehensive scans of systems, networks, and applications. OpenVAS offers a user-friendly interface and provides detailed reports on vulnerabilities found. Being open-source, it is constantly updated and improved by a large community of developers worldwide.
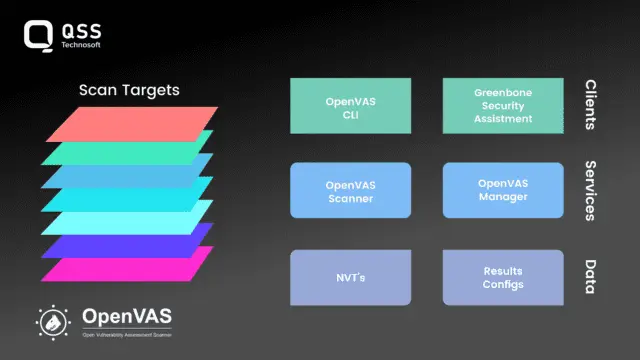
Benefits:
- Open-Source and Community-Driven: OpenVAS is an open-source vulnerability scanner supported by a large community of developers, ensuring regular updates, improvements, and customization options.
- Versatile Scanning Capabilities: The tool allows users to conduct comprehensive scans of systems, networks, and applications, making it suitable for a wide range of testing scenarios.
- User-Friendly Interface: OpenVAS provides a user-friendly interface, making it accessible to both novice and experienced security professionals.
- Detailed Reports: It generates detailed reports on vulnerabilities found, including recommendations for remediation, helping organizations understand and prioritize the identified weaknesses.
- Easy Integration: OpenVAS comes with APIs and plugins that enable it to be easily integrated into existing security workflows and toolsets.
4. Metasploit
Metasploit is a popular penetration testing tool that provides a wide range of exploits and payloads. It allows security professionals to simulate real-world attacks and test the effectiveness of their defenses. Metasploit also offers an extensive database of vulnerabilities and their corresponding exploits, making it a valuable resource for penetration testers.
Benefits:
- Wide Range of Exploits and Payloads: Metasploit offers an extensive database of exploits and payloads, enabling security professionals to simulate real-world attacks and test the effectiveness of their defenses.
- Rapid Testing: The tool allows for quick testing of vulnerabilities, reducing the time required for the assessment and enabling security teams to respond promptly to address identified weaknesses.
- Detailed Penetration Testing Reports: Metasploit generates detailed reports on the results of penetration testing, providing valuable insights and recommendations for improving security.
- Community Support: It benefits from an active and passionate community that contributes to its continuous development, ensuring that users have access to the latest exploits and techniques.
- Integration: Metasploit can be easily integrated with other security tools and platforms, enhancing the overall effectiveness of vulnerability assessment and penetration testing processes.
Read Also: How to Build an App like Exodus Cryptocurrency Wallet?
5. Wireshark
Wireshark is a network protocol analyzer that helps security professionals capture and analyze network traffic. It allows users to inspect packets in detail, identify anomalies, and detect potential vulnerabilities. Wireshark is particularly useful during penetration testing, as it provides insights into network behavior and allows for the identification of potential weak points.
Benefits:
- Packet-level Analysis: Wireshark allows security professionals to capture and analyze network traffic at the packet level, providing deep insights into network behavior and potential vulnerabilities.
Anomaly Detection: The tool helps identify anomalies in network traffic, highlighting potential security breaches or misconfiguration.
- Protocol Support: Wireshark supports a wide range of protocols, making it versatile for analyzing and identifying vulnerabilities across various network protocols.
- Real-Time Monitoring: It provides real-time monitoring capabilities, allowing security teams to detect and respond to threats or vulnerabilities promptly.
- Educational Resource: Wireshark is not only a tool for vulnerability assessment but also serves as an educational resource for understanding network protocols and their security implications.
6. Burp Suite
Burp Suite is a web application security testing tool that assists security professionals in identifying vulnerabilities in web applications. It provides a wide range of features, including scanning for common web application vulnerabilities, intercepting and modifying web traffic, and performing automated security tests. Burp Suite is highly versatile and can be integrated into the development process to ensure secure coding practices.
Benefits:
- Advanced Web Application Scanning: Burp Suite offers advanced scanning capabilities specifically tailored for web applications, helping security professionals identify vulnerabilities in this critical area.
- Traffic Interception and Modification: The tool allows for the interception and modification of web traffic, enabling security teams to analyze and manipulate requests and responses for discovering potential vulnerabilities.
- Automated Security Testing: Burp Suite supports automated security testing, allowing for the continuous assessment of web applications during development cycles.
- Integration with Development Process: It can be seamlessly integrated into the development process, encouraging secure coding practices by providing real-time feedback to developers.
- Extensibility: Burp Suite offers an extensible framework that allows users to develop and customize their own plugins to tailor the tool to their specific needs and requirements.
Read Also: Cutting AWS Costs with IPv6: A Comprehensive Guide to Migrating from IPv4 to IPv6 for Elastic IPs
7. Nikto
Nikto is an open-source web server scanner that helps security professionals identify security flaws in web servers. It can scan for more than 6700 potentially dangerous files and programs, providing users with a comprehensive overview of vulnerabilities. Nikto also checks for misconfigurations and outdated software versions, helping organizations maintain a secure web server environment.
Benefits:
- Extensive Web Server Scanning: Nikto scans web servers for more than 6700 potentially dangerous files and programs, providing a comprehensive overview of vulnerabilities within web server environments.
- Misconfiguration Detection: The tool also checks for misconfigurations, ensuring that web servers are properly configured for optimal security.
- Outdated Software Detection: Nikto helps identify outdated software versions on web servers, which are often prone to known vulnerabilities.
- Open-Source and Free: Being an open-source tool, Nikto is freely available, making it accessible to security professionals with limited budgets.
- Command-Line Interface: Nikto’s command-line interface makes it suitable for automation and integration with other security tools or scripts.
8. Aircrack-ng
Aircrack-ng is a suite of tools designed for wireless network auditing and penetration testing. It can assess the security of wireless networks by capturing packets, cracking WEP and WPA/WPA2-PSK keys, and performing various attacks. Aircrack-ng is particularly useful for organizations that rely heavily on wireless networks, as it helps identify and address potential security vulnerabilities in their wireless infrastructure.
Benefits:
- Wireless Network Auditing: Aircrack-ng specializes in wireless network auditing, allowing security professionals to assess the security of wireless networks for potential vulnerabilities.
- Packet Capture: The tool captures and analyzes wireless network packets, helping identify potential security weaknesses or unauthorized access attempts.
- Key Cracking: Aircrack-ng can crack WEP and WPA/WPA2-PSK keys, assisting in evaluating the strength of wireless network encryption.
- Penetration Testing: It enables security teams to simulate attacks on wireless networks, providing valuable insights into their security posture.
- Active Community: Aircrack-ng benefits from an active community of developers and users, ensuring regular updates, improvements, and access to community-driven tools and utilities.
Conclusion
Vulnerability assessment and penetration testing are critical processes that organizations should conduct regularly to ensure the security of their infrastructure. The tools mentioned in this blog post are among the top choices for security professionals when it comes to carrying out these tests effectively. Each tool offers unique features and capabilities, enabling organizations to identify and address vulnerabilities in their systems, networks, and applications promptly.
However, it is important to note that the effectiveness of these tools depends on the skill and expertise of the security professionals using them. Therefore, organizations should invest in well-trained and knowledgeable individuals who can leverage these tools effectively and interpret the results accurately. By doing so, organizations can enhance their security posture and protect themselves from potential cyber threats.
We are proud to mention that our work has been recognized by leading B2B reviews and research platforms like GoodFirms, Clutch, MirrorView, and many more.


Top Tools for Effective Vulnerability Assessment and Penetration Testing