Hey! Do you know the way commonplace cyber threats have turned out to be? With the growing number of cybersecurity assaults, companies throughout all industries are dealing with extensive risks to their networks and sensitive information (dangerous right?). It is essential that organizations be ahead of any weaknesses in their infrastructure within the community. Vulnerability Assessment & Penetration Testing (VAPT) is one efficient technique. This assists us in identifying any vulnerabilities and addressing them before malevolent actors take advantage of them. Thus, let us ensure that we each play a part in maintaining the safety and security of our community’s infrastructure.
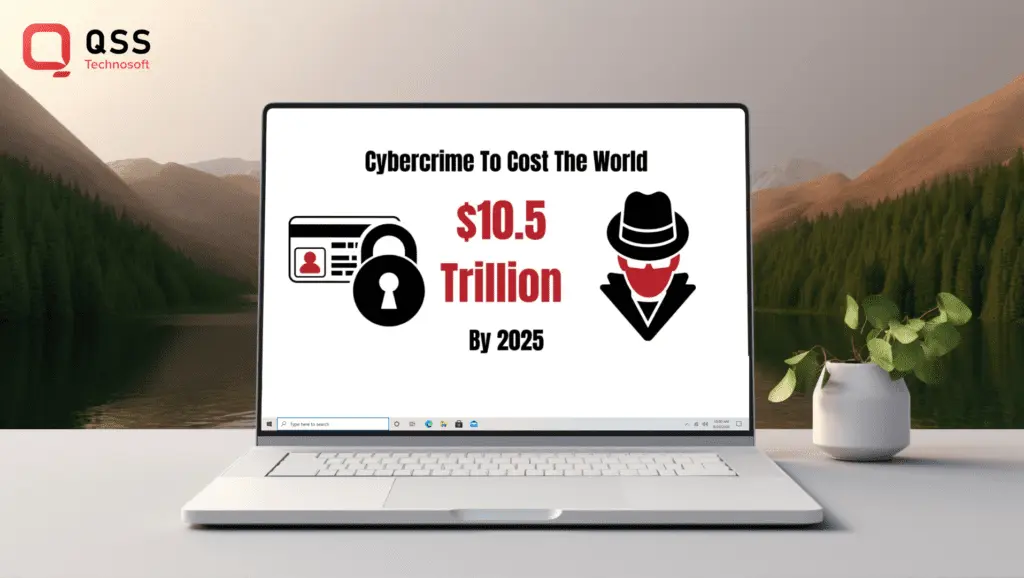
In fact, you will be surprised to know that the need for VAPT has become even more urgent when considering the staggering statistics surrounding cybercrime. It is estimated that by 2025, cybercrime damages will cost the world a whopping $10.5 trillion annually, according to a report by Cybersecurity Ventures. This emphasizes the critical nature of implementing robust security measures and regularly assessing network vulnerabilities.
To put it into perspective, consider a hypothetical multinational company that stores sensitive customer data on its servers. Without proper VAPT, they could be unknowingly exposing their customers’ valuable information to cybercriminals. However, by conducting vulnerability assessments and penetration testing, they can identify and address vulnerabilities, strengthening their overall security posture and safeguarding customer data.
Ultimately, implementing a diligent VAPT strategy is essential for organizations looking to mitigate the risks posed by cyber threats. In this blog, we will help you to understand about demystifying vulnerability assessment and penetrating testing. So, make sure don’t skip and read this till the end.
What is Vulnerability Assessment & Penetration Testing?
What exactly is VAPT, and how can it help organizations protect themselves from cyber threats? By conducting a thorough analysis of their network, VAPT helps businesses identify potential weaknesses and vulnerabilities that could be exploited by malicious actors. Through the use of vulnerability assessments and penetration testing, organizations can discover and address security flaws and potential entry points before they can be exploited.
Vulnerability Assessment involves using automated tools to scan an organization’s network, systems, and applications for known vulnerabilities, misconfigurations, and weaknesses. It provides a systematic review of the vulnerabilities present and their severity level. Vulnerability assessment helps organizations understand their current security posture and prioritize vulnerabilities for remediation.
Example:
- Network Scanner: A network scanning tool like Nmap can be used to identify open ports, protocols, and services running on various network devices. It can help identify vulnerabilities such as outdated services or insecure configurations that may leave the network exposed.
- Web Application Scanner: Tools like OWASP ZAP or Burp Suite can be used to assess the security of web applications. These tools can scan for common vulnerabilities like SQL injection, cross-site scripting (XSS), or insecure direct object references (IDOR), and provide a detailed report of potential weaknesses.
- Penetration Testing, also known as ethical hacking, goes beyond vulnerability assessment. It involves simulating real-world attacks to exploit vulnerabilities discovered during the assessment phase. Penetration testers try to gain unauthorized access to systems, applications, or network infrastructure to assess the impact of a successful attack and identify potential entry points for attackers.
Example
- Password Cracking: During a penetration test, ethical hackers may use tools like John the Ripper or Hashcat to crack passwords. This helps test the strength of the organization’s password policy and identify weak passwords that could be easily exploited by attackers.
- Social Engineering: Penetration testers may use social engineering techniques, such as phishing emails or phone calls, to trick employees into revealing sensitive information or performing actions that could compromise security. This helps assess the effectiveness of the organization’s security awareness training and policies.
Read Also: Top 10 Custom App Ideas for Salesforce
Why is Vulnerability Assessment & Penetration Testing important?
With cybercriminals becoming more sophisticated, organizations must stay one step ahead of the game when it comes to security. VAPT offers several benefits that contribute to an organization’s overall cybersecurity strategy:
Identify vulnerabilities:
VAPT helps organizations uncover vulnerabilities that could be exploited by attackers. For instance, a vulnerability assessment might reveal an insecure configuration in a web server software, allowing an attacker to perform remote code execution and gain unauthorized access to the server.
Compliance requirements:
Many regulatory frameworks mandate VAPT as a requirement for compliance. For example, the HIPAA Security Rule in the healthcare industry mandates regular VAPT assessments to protect electronic protected health information (ePHI) from unauthorized access. Failure to comply can result in heavy fines and legal consequences.
Reduce risk exposure:
VAPT assists in minimizing the risk of successful cyber attacks. For instance, a penetration test might uncover an unpatched vulnerability in a network router, which, if exploited, could enable an attacker to gain control of the entire network and exfiltrate sensitive data.

Build customer trust:
Through VAPT, organizations can demonstrate their commitment to data security to build customer trust. For instance, a financial institution that regularly undergoes VAPT assessments can assure customers that their online banking platform is continuously evaluated for vulnerabilities and is secure against threats like account takeover or fraud.
Test incident response capabilities:
VAPT assessments allow organizations to test their incident response plans and identify areas of improvement. For instance, a simulated phishing attack during a VAPT engagement can determine how well employees detect and report such attempts, helping organizations reinforce security awareness training and response procedures.
Detecting zero-day vulnerabilities:
VAPT helps identify zero-day vulnerabilities, which are unknown vulnerabilities that have not yet been discovered by the software vendor. By finding these vulnerabilities before cybercriminals do, organizations can take proactive measures to patch or mitigate the risk associated with them. For example, a VAPT assessment could uncover a zero-day vulnerability in a web application’s code, allowing the organization to deploy patches or implement additional security measures to protect against potential attacks.
Assessing IoT device security:
The proliferation of Internet of Things (IoT) devices introduces new complexities to cybersecurity. VAPT can help identify vulnerabilities in IoT devices and associated infrastructure, such as weak authentication mechanisms, insecure communication protocols, or unpatched firmware. Identifying these vulnerabilities allows organizations to address the security risks associated with IoT devices and protect critical systems from potential compromise.
Read Also: How to Build an App like Trezor Cryptocurrency Wallet?
The Steps of Vulnerability Assessment & Penetration Testing Process
This process involves a comprehensive analysis of potential weaknesses that could be exploited by malicious actors. By conducting VAPT, organizations can proactively address these vulnerabilities and minimize the risk of cyber attacks.
Step 1: Planning and Scoping
The first step in the VAPT process is planning and scoping. It involves defining the objectives of the assessment, identifying the target systems, and determining the method and approach for conducting the assessment. The scope of the assessment should be clearly defined to ensure that all critical systems are included.
Method and approach for conducting the assessment.
Examples:
- Determining the total number of devices that will be included in the assessment, including servers, routers, switches, and other hardware devices
- Identifying the IP addresses of the target systems and the specific applications that need to be assessed.
How this work?
- Define the scope of the assessment in a formal document.
- Determine the testing methodology, including the tools and techniques to be used.
- Define the timeline and schedule for the assessment.
Step 2: Vulnerability Assessment
The vulnerability assessment phase involves identifying and assessing weaknesses in the target systems. This can be done through various methods such as automated scanning tools, manual testing, and source code analysis. The goal is to uncover potential vulnerabilities, misconfigurations, and insecure coding practices that could be exploited.
Examples:
- Conducting a port scan and identifying open ports and services on the target system
- Running a vulnerability scanner to identify known vulnerabilities and misconfiguration
- Conducting a web application assessment to identify issues with the application’s code or configuration.
How does this work?
- Ensure that all relevant systems are included in the assessment
- Utilize a variety of testing methods and tools to identify all possible vulnerabilities
Step 3: Penetration Testing
Once the vulnerabilities are identified, the next step is penetration testing. This involves actively exploiting the vulnerabilities in a controlled manner to test the security controls and measure the impact of a potential attack. Penetration testing can be conducted in various ways, including network-based, application-based, and physical testing.
Examples:
- Conducting a phishing attack to test employee awareness and identify weaknesses in email security controls
- Running a SQL injection attack on a web application to test the effectiveness of the security controls
- Using a password cracking tool to test the strength of user passwords.
How does this work?
- Conduct controlled attacks that mimic real-world attack scenarios
- Document all testing parameters and ensure that all testing is conducted ethically and within legal boundaries.
Step 4: Analysis and Reporting
After completing the vulnerability assessment and penetration testing, the data collected needs to be analyzed to determine the level of risk posed by the identified vulnerabilities. This analysis will help prioritize the vulnerabilities based on their severity and the potential impact on the organization’s systems and data. A detailed report should be generated, outlining the vulnerabilities found and providing recommendations for remediation.
Examples:
- Conducting a risk analysis to determine the likelihood and potential impact of each identified vulnerability
- Prioritizing vulnerabilities based on their severity and the potential impact on the organization
- Developing a formal report that includes recommendations for remediation.
How does this work?
- Review all test findings to ensure that nothing was overlooked
- Document all test results in a formal report, including any supporting documentation or evidence gathered during testing
Read Also : Guide & Cost to Develop YouTube Like App
Step 5: Remediation
The remediation phase involves addressing the identified vulnerabilities and implementing the recommended fixes. This could involve patching systems, reconfiguring settings, updating software, or fixing coding errors. It is essential to prioritize the vulnerabilities based on their severity to ensure that the most critical ones are addressed first.
Examples:
- Applying security patches to systems and applications
- Implementing secure configuration settings on systems and devices
- Updating security controls, such as firewalls and intrusion detection systems.
How does this work?
- Make sure all vulnerabilities are addressed in a timely manner
- Test remediation measures to ensure that they are effective and do not introduce new vulnerabilities.
Step 6: Reassessment
Once the remediation measures have been implemented, it is crucial to conduct a reassessment to verify that the vulnerabilities have been effectively patched and mitigated. This reassessment can include repeat vulnerability scanning and targeted penetration testing. It helps ensure that all identified vulnerabilities have been adequately addressed and that the systems are secure.
Examples:
- Conducting a repeat vulnerability scan to verify that all identified vulnerabilities have been resolved
- Re-running penetration testing to ensure that the remediation measures have effectively mitigated the identified vulnerabilities.
How does this work?
- Ensure that all tests are conducted using the same methods and tools used in the original assessment
- Document all test results in a formal report and provide recommendations for any additional remediation measures if necessary.
Conclusion
Adapting Vulnerability Assessment and Penetration Testing (VAPT) isn’t just a security measure – it’s a proactive stance against cyber predators lurking in the digital shadows. Remember, in the world of cybersecurity, staying one step ahead is the name of the game.
So, if you’re ready to fortify your defenses, enhance your security posture, and send cybercriminals packing, take the first step with QSS Technosoft. Contact our experts today to turn your organization into a cyber fortress that even the most determined hackers would think twice before challenging!
We are proud to mention that our work has been recognized by leading B2B reviews and research platforms like GoodFirms, Clutch, MirrorView, and many more.


Why Vulnerability Assessment and Penetration Testing (VAPT) is Crucial for Your Business Overall Security?