The evolution of artificial intelligence (AI) has brought about many advancements in technology in recent years. How has AI transformed various industries, from self-driving cars to personal assistants? One notable area where AI-driven cybersecurity has made significant strides . With its ability to identify and flag potential threats, AI has become a powerful tool in defending against cyber attacks. However, this same technology poses a unique challenge.
How can we address the potential misuse of AI by attackers, who can use its capabilities to create more sophisticated and harder-to-detect attacks? Let’s take a quick example, imagine a scenario where AI-powered malware adapts and evolves in real-time, making it increasingly difficult for traditional security measures to keep up.
The Challenge of Generative AI
Generative AI, in particular, has become a growing concern for cybersecurity experts. This type of AI is designed to mimic human creativity and generate content such as images, videos, and audio.
While this may seem harmless, generative AI can also be used to create fake content that is difficult to distinguish from the real thing.
One example of generative AI is a deepfake video being used to damage a politician’s reputation is the case of Gabon’s President Ali Bongo. In 2018, a deepfake video went viral on social media, showing a supposedly healthy Bongo delivering a New Year’s message to the nation. However, in reality, Bongo had suffered a stroke and was unable to speak at the time.
Read Our Old Blog : Exploring the Impact of Generative AI in Design and Content Creation
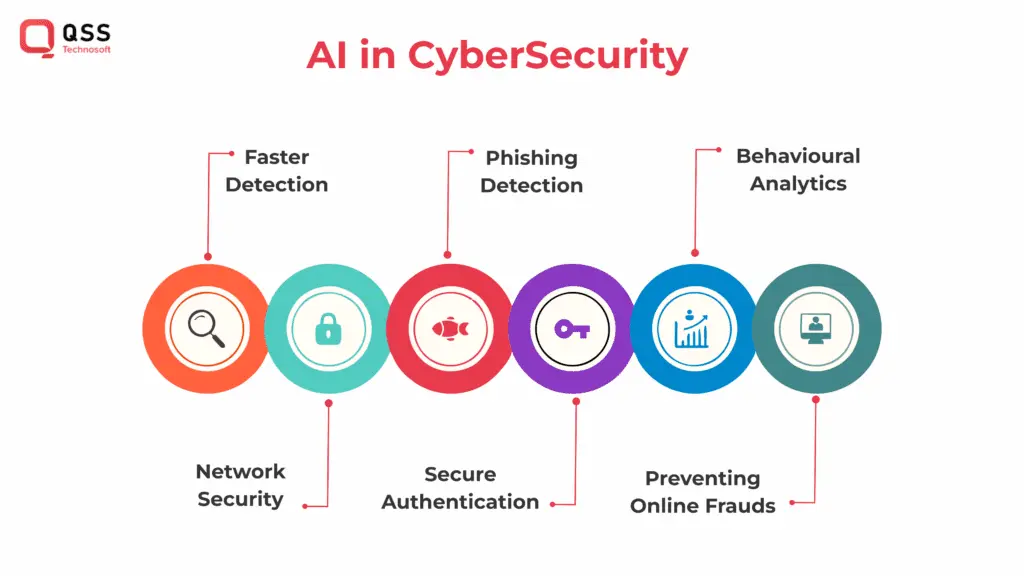
The Benefits of AI-Driven Cybersecurity
AI-driven cybersecurity has several advantages over traditional methods, including:
a.Ephemeral Messaging
AI can analyze va1. Speed and Accuracyst amounts of data in real-time and identify potential threats much faster than a human can. AI can also learn and adapt to new threats, making it a valuable tool for staying ahead of attackers.
For example, the IBM Watson for Cyber Security uses AI to analyze vast amounts of threat data, enabling it to rapidly detect and respond to cyber threats with greater accuracy than traditional methods.
2. Predictive Analytics
With machine learning algorithms, AI can identify patterns and anomalies in data that may be indicative of a cyber attack. This allows organizations to prevent attacks before they occur.
For instance, Darktrace’s Enterprise Immune System leverages unsupervised machine learning to learn and understand “normal” behavior on a network, enabling it to quickly detect any abnormal activities that could be indicative of a cyber attack.
3. Automation
AI can automate many mundane and repetitive tasks, such as patching software or monitoring network traffic. This frees up cybersecurity professionals to focus on more strategic initiatives.
Palo Alto Networks’ Cortex XSOAR allows organizations to automate incident response activities, such as data enrichment, threat hunting, and remediation. This helps in improving efficiency and response time in handling security incidents.
4. Scalability
With AI-driven cybersecurity solutions, organizations can easily scale their cybersecurity efforts as their needs grow.
For example, CrowdStrike’s Falcon platform uses AI to protect endpoints and can seamlessly scale its protection across thousands of devices, making it suitable for organizations of all sizes, from small businesses to large enterprises.
Steps to Adopting AI-Driven Cybersecurity
Implementing AI-driven cybersecurity solutions may seem daunting, but with the right strategy, it can be a smooth transition.
Here are some steps organizations can take to adopt AI-driven cybersecurity:
1. Assess Current Cybersecurity Capabilities
Before implementing any new technology, it’s essential to assess the current state of cybersecurity within the organization. This includes evaluating existing tools, processes, and policies for identifying and mitigating cyber threats.
2. Identify Gaps and Opportunities for Improvement
Once the current state of cybersecurity is assessed, the next step is to determine where the organization’s cybersecurity capabilities fall short. This could include identifying blind spots in security monitoring or gaps in threat intelligence gathering. This information can then be used to identify opportunities for improvement and where AI-driven solutions may be most beneficial.
3. Develop a Roadmap for Implementation
4. Determine the Appropriate AI-Driven Solutions
After identifying where AI-driven cybersecurity solutions can be most effective, organizations should develop a roadmap for implementation. This includes determining the scope of the project, developing a timeline, and identifying the necessary resources and personnel.
There are many different AI-driven cybersecurity solutions available, and it’s essential to choose the appropriate solution for the organization’s needs. This may include solutions designed for threat detection, response, or automation.
5. Integrate AI-Driven Solutions into Existing Processes
Once the appropriate solutions are identified, they must be integrated into existing security processes. This may require changes to existing policies, procedures, and training programs.
Read our Old Blog : How AI Tools like ChatGPT is Solving Top Industry Challenges?
Challenges in Implementing AI-Driven Cybersecurity
While AI-driven cybersecurity solutions offer many benefits, they also present unique challenges. Some of these challenges include:
1. Lack of Talent
Implementing AI-driven cybersecurity solutions requires skilled personnel who understand both AI and cybersecurity. However, there is a shortage of qualified cybersecurity professionals, making it difficult for organizations to find the talent they need. For example, a study by ESG and ISSA found that 51% of surveyed organizations reported a “problematic shortage” of cybersecurity skills in 2019.
2. Data Quality
AI relies on large amounts of high-quality data to learn and improve. If data is inaccurate or incomplete, AI-driven solutions may not be effective. For instance, if a machine learning model uses biased data to identify intrusions, it may unintentionally discriminate against certain user groups, leading to false positives or negatives.
3. Integration Complexity
Integrating AI-driven solutions into existing security processes can be complex. It requires expertise in both AI and cybersecurity and may require changes to existing processes and policies. Furthermore, organizations may need to make changes to their existing processes and policies to accommodate the new technology. The complexity of integration can be a barrier for some organizations.
4. False Positives
AI-driven solutions may generate false positives, causing unnecessary alerts and wasting cybersecurity professionals’ time. For example, an AI system that is overly sensitive to anomalies may trigger numerous false alerts, leading to wasted time and resources in investigating and addressing these false positives.
Conclusion
AI-driven cybersecurity is an essential tool in the fight against cyber attacks in the age of generative AI. At QSS Technosoft, we understand that adopting AI-driven cybersecurity solutions can be challenging. That’s why we offer a strategic roadmap for implementation, ensuring seamless integration, data quality, and talent acquisition. Our team of experts will guide you through the process, ensuring a successful and effective transition.
Don’t compromise your organization’s security in the face of advanced cyber attacks. Contact QSS Technosoft today and fortify your defences with AI-driven cybersecurity solutions. Stay ahead of the curve and protect your business from emerging threats.
We are proud to mention that our work has been recognized by leading B2B reviews and research platforms like GoodFirms, Clutch, MirrorView, and many more.



AI-Driven Cybersecurity: Mitigating Threats in the Age of Generative AI