Table of Contents
- Summary
- Introduction
- Understanding Security Testing
- 1. Vulnerability Assessment
- 2. Penetration Testing
- 3. Security Code Review
- 4. Security Architecture Review
- 5. Ethical Hacking
- 6. Posture Assessment
- 7. Security Auditing
- Reasons Why Security Testing is Important?
- 1. Protection against potential breaches
- 2. Safeguarding sensitive data
- 3. Compliance with regulatory requirements
- 4. Maintaining customer trust
- 5. Cost savings in the long run
- 6. Identifying system weaknesses
- 7. Staying ahead of evolving threats
- Types of Security Testing and When to Use Them
- Web Application Security Testing
- Mobile Application Security Testing
- Network Penetration Testing
- Cloud Security Testing
- Software Composition Analysis (SCA)
- Static Application Security Testing (SAST)
- Dynamic Application Security Testing (DAST)
- Interactive Application Security Testing
- Common Security Testing Tools Used
- Challenges in Security Testing
- Keeping Up with Evolving Threats
- False Positives from Automated Tools
- Lack of Skilled Cybersecurity Professionals
- Testing Without Disrupting Production Systems
- Best Practices for Conducting Effective Security Testing
- Dos
- Don'ts
- How QSS Technosoft Helps Secure Your Digital Infrastructure
- Our Service Offerings Include
- Success Stories
- Conclusion
- FAQs Section
Summary
This blog highlights the growing importance of security testing in protecting digital systems against increasingly sophisticated cyber threats, projected to cause $10.5 trillion in damages annually by 2025. It explains different types of security testing—such as vulnerability assessment, penetration testing, security code review, and cloud security testing—and when to use them. The post emphasizes the benefits, including breach prevention, safeguarding sensitive data, ensuring regulatory compliance, building customer trust, and achieving long-term cost savings. It also addresses challenges like evolving threats, false positives, and skill shortages, while offering best practices for effective testing. QSS Technosoft’s expertise in VAPT, compliance testing, audits, and ongoing monitoring is showcased through real-world success stories. The conclusion urges businesses to prioritize security testing as a core strategy for resilience in the digital age.
Introduction
Are you aware that in this technology-growing world, the safety of our virtual systems and applications performs an immensely big position in our everyday lives? Because who wants to compromise with their digital information? With the non-stop evolution and increasing sophistication of generation, common cyber threats focused on susceptible systems are at the upward rise. Recent statistics showcased us that the worldwide price of cybercrime is projected to reach a spectacular $10.5 trillion annually via 2025, as mentioned by way of Cybersecurity Ventures This statistic serves as a stark reminder of the pressing need for complete security Testing as well as checking-out practices to combat cyber threats efficiently. Traditional defenses like antivirus software are no longer sufficient because cyber threats have become more sophisticated, often evading signature-based detection. Modern attacks require advanced security testing and proactive security measures, including leveraging artificial intelligence, to identify and mitigate evolving vulnerabilities effectively.
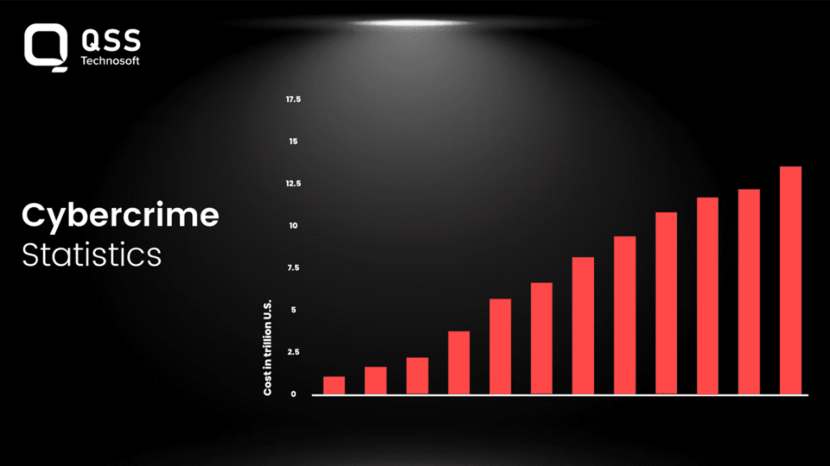
So, how are we able to ensure the safety and protection of our virtual assets?
When it comes to defending our sensitive information and stopping cyber-attacks, safety is emerging as a critical line of protection. By very well evaluating software programs, structures, and networks, protection checking out goals to pick out vulnerabilities and weaknesses that could be exploited by hackers.
This proactive approach is crucial in safeguarding our digital systems and ensuring the confidentiality and data integrity
Make sure to read this blog till the end because today we are going to provide you a guide on why security testing is important.
Read Also: Uncover the 15 Best Testing Practices for Salesforce App Development
Understanding Security Testing
Security testing is a process that assesses an organization's security posture and helps identify potential vulnerabilities and risks. It involves testing software applications, networks, and systems to ensure that they are secure and free from vulnerabilities that could be exploited by attackers. It can be conducted either manually or through automated tools. Additionally, security testing evaluates the effectiveness of backup systems to ensure data availability and recovery in case of security incidents.
Real-life examples of security testing include penetration testing, vulnerability scanning, and risk assessments.
- For instance, a company might hire a security testing firm to conduct a penetration test on their network to identify vulnerabilities that could be exploited by cybercriminals.
- Alternatively, they may use a vulnerability scanning tool to automatically scan their systems for known vulnerabilities and weaknesses.
- Finally, a risk assessment would be conducted to identify potential risks and security threats to a company's security posture and help develop a mitigation strategy.
There are several different types of security testing that can be utilized, depending on the specific needs of an organization. These include:
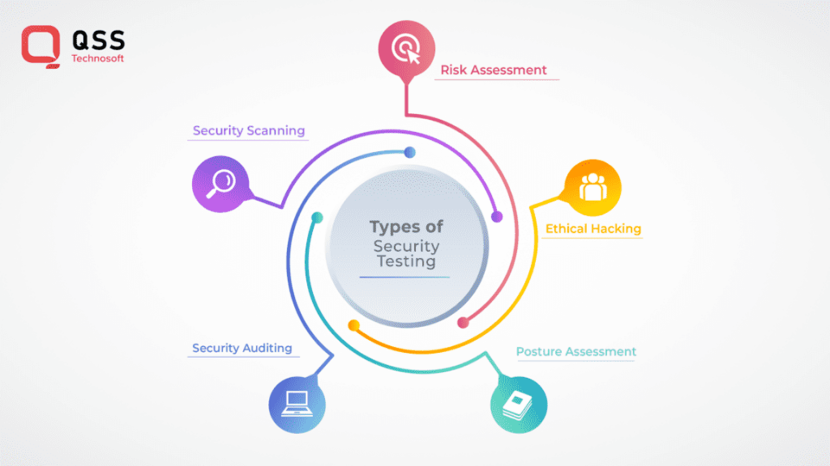
1. Vulnerability Assessment
Vulnerability assessment is a systematic process of identifying and prioritizing vulnerabilities within a system or application. It involves the use of automated tools and techniques to scan for common vulnerabilities, such as weak passwords, outdated software, misconfigured system components, or insider threats. By conducting regular vulnerability assessments, organizations can identify and address potential security weaknesses before they are exploited.
2. Penetration Testing
Penetration testing, commonly known as ethical hacking, involves simulating real-world attacks to evaluate the effectiveness of the organization's security controls. It helps organizations understand how their systems would respond to an actual attack and identifies potential security gaps. By mimicking the techniques used by hackers, including those deploying malicious software, organizations can proactively address vulnerabilities and strengthen their security posture.
3. Security Code Review
Security code review is a manual or automated process of examining the source code of an application to identify potential security vulnerabilities. This process involves analyzing the code for common coding errors, such as buffer overflows or SQL injection vulnerabilities. By conducting code reviews, developers can identify and fix security issues early in the development cycle, reducing the chances of vulnerabilities being introduced into the production environment and thereby protecting systems from potential attacks..
4. Security Architecture Review
Security architecture review is an evaluation of the overall security design of a system or application. It assesses whether the implemented security controls are appropriate and effective in mitigating potential risks. By reviewing the security architecture, organizations can ensure that security controls are implemented in a way that aligns with industry best practices and security standards, thereby helping to protect critical infrastructure from cyber threats.
5. Ethical Hacking
Ethical hacking, also known as penetration testing or white hat hacking, is a legal and authorized practice of assessing the security of an organization's systems, networks, and applications. Ethical hackers are skilled professionals who use the same techniques and tools as malicious hackers to identify vulnerabilities and weaknesses in order to help improve the organization's security defenses and ensure that only authorized users can gain access to sensitive customer data.
6. Posture Assessment
Posture assessment, also known as vulnerability assessment, is the process of evaluating an organization's security posture to identify potential weaknesses or vulnerabilities. This assessment involves collecting information about the organization's network infrastructure, systems, and applications and analyzing them to determine if any security gaps exist.
7. Security Auditing
Security auditing is an independent evaluation of an organization's sensitive information systems, policies, procedures, and controls to assess their effectiveness in mitigating security risks. It involves reviewing the organization's security program, conducting interviews with key personnel, and examining evidence such as system logs and configuration files. This process is essential not only for protecting corporate assets but also for supporting national security by ensuring critical infrastructure and sensitive data are safeguarded against cyber threats.
Read Also: How to Build an App like Trezor Cryptocurrency Wallet?
Reasons Why Security Testing is Important?
Lets understand key reasons why security testing is important.
1. Protection against potential breaches
One of the primary reasons why security testing is crucial is that it helps protect against potential breaches. In the realm of cybersecurity in the digital age, by simulating real-world attack scenarios, security testing identifies vulnerabilities in a system that attackers could exploit. By addressing these vulnerabilities before deployment, organizations can significantly reduce the risk of a breach and the subsequent damage it can cause.
2. Safeguarding sensitive data
Sensitive data, such as customer information, financial data, and intellectual property, is a prime target for hackers. Security testing help ensures that this sensitive data is adequately protected by identifying any weaknesses in the system's security controls. By strengthening these attribute based access control, organizations can minimize the risk of data breaches and the resulting reputational and financial damage.
3. Compliance with regulatory requirements
With the increasing number of laws and regulations governing data privacy and security, organizations must comply with these requirements. Security testing plays a vital role in ensuring compliance with regulations such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). By conducting security tests, organizations can identify any compliance gaps and take appropriate actions to rectify them.
4. Maintaining customer trust
Customer trust is a cornerstone of any successful business. If customers do not feel confident in the security of a product or service, they will be reluctant to engage with the organization. Security testing provides reassurance to customers that their data is being adequately protected. By demonstrating a commitment to security, organizations can build and maintain trust with their customers, leading to increased customer loyalty and satisfaction.
5. Cost savings in the long run
While security testing may require additional resources and investment upfront, it can result in significant cost savings in the long run. Addressing security vulnerabilities early in the development process is far less costly than dealing with the repercussions of a breach, which can include financial losses, legal expenses, and damage to the organization's reputation. By investing in security testing, organizations can prevent potential breaches and save themselves from costly cleanup business operations down the line.
6. Identifying system weaknesses
Security testing goes beyond identifying vulnerabilities in software applications. It also helps identify weaknesses in the overall system architecture, network infrastructure, and employee behavior. This holistic approach ensures that all aspects of an organization's security posture are evaluated and improved. By addressing system weaknesses, organizations can prevent potential breaches from occurring and strengthen their overall security posture.
7. Staying ahead of evolving threats
The threat landscape is constantly evolving, with attackers developing new techniques and tactics to breach systems. Security testing helps organizations stay ahead of these threats by simulating real-world attack scenarios and identifying potential weaknesses in the system. By proactively addressing these weaknesses, organizations can significantly reduce the risk of falling victim to emerging threats, and security testing helps ensure they are well-prepared to defend against evolving attack vectors.
Read Also: How to Build an App like Exodus Cryptocurrency Wallet?
Empower Your Digital Vision with an Award-Winning Tech Partner
QSS Technosoft is globally recognized for innovation, excellence, and trusted delivery.
- Clutch Leader in App Development 2019
- Ranked Among Top 100 Global IT Companies
- Honored for Cutting-edge AI & Mobility Solutions
Types of Security Testing and When to Use Them
Ethical hacking simulates attacks on a system to identify vulnerabilities, done with the organization's consent to improve security. It is also known as penetration testing or white-hat hacking and is carried out by certified professionals using the same methods as malicious hackers to strengthen system defenses.
Web Application Security Testing
Web application testing focuses on identifying vulnerabilities such as SQL injection and cross-site scripting (XSS) that attackers could exploit to gain unauthorized access or manipulate data. For example, testing a banking website to ensure input fields are properly sanitized helps prevent attackers from injecting malicious code.
Mobile Application Security Testing
Mobile app security testing examines native, hybrid, and progressive web apps (PWAs) for vulnerabilities like insecure data storage, weak authentication, and the absence of multi factor authentication. For instance, testing a mobile payment app to detect if sensitive user data is securely stored and transmitted protects against data breaches.
Network Penetration Testing
Network penetration testing evaluates firewalls, routers, and internal networks to uncover weaknesses that could allow unauthorized access or lateral movement. A real-world scenario includes testing an enterprise network to identify misconfigured firewall rules that could expose critical systems.
Cloud Security Testing
Cloud security testing assesses cloud environments for issues such as identity and gain access management (IAM) misconfigurations and publicly accessible storage buckets. For example, testing a cloud storage service to ensure buckets are not open to public access helps prevent data leaks.Dynamic application security testing evaluates applications while they are running to identify security vulnerabilities that could be exploited by attackers in real time, providing a crucial layer of defense in modern security testing strategies.
Software Composition Analysis (SCA)
Software Composition Analysis (SCA) identifies vulnerabilities in third-party components used in a software application.Many modern applications rely on open-source libraries and third-party frameworks. SCA tools scan these dependencies to detect known vulnerabilities, licensing issues, and outdated components that could compromise the application’s security.
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) is a method of security testing that analyzes source code for vulnerabilities without executing the application. It helps developers identify and fix security flaws early in the software development lifecycle, reducing the risk of security breaches. SAST integrates with development environments to provide real-time feedback, promoting secure coding practices. Security testing tools like SAST are essential in automating and enhancing the effectiveness of these assessments.
Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) evaluates applications while they are running to identify security vulnerabilities. It tests the application from the outside in, mimicking how an attacker would interact with the application in real-time. DAST is particularly effective at finding issues like input/output validation flaws, authentication problems, and configuration errors during testing. Additionally, runtime application self-protection (RASP) complements DAST by providing real-time monitoring and defense within the application, detecting and mitigating attacks as they occur to enhance overall security .
Interactive Application Security Testing
Interactive Application Security Testing (IAST) combines the strengths of static and dynamic testing methods to analyze applications in real-time during runtime. It provides continuous feedback on security vulnerabilities by monitoring code execution and user interactions. IAST helps security professionals identify and remediate complex security issues more efficiently within the software development lifecycle. Security testing tools SAST play a crucial role in this process by analyzing source code to detect vulnerabilities early, complementing IAST's dynamic analysis capabilities. This approach significantly enhances the detection and mitigation of evolving security threats, ensuring a more robust defense against potential attacks.
Common Security Testing Tools Used
Security professionals rely on a variety of specialized tools to identify security vulnerabilities and assess the overall security posture of systems and applications. Metasploit is a powerful penetration testing framework that simulates real-world attacks to uncover security flaws. Nessus is widely used for vulnerability scanning, helping detect known weaknesses across networks and devices. SQLMap automates the detection and exploitation of SQL injection vulnerabilities in web applications. MobSF (Mobile Security Framework) focuses on mobile application security testing, analyzing apps for insecure data storage and other mobile-specific risks. Intruder is a cloud-based vulnerability scanner that continuously monitors digital assets for emerging threats. Burp Suite is an integrated platform for web application security testing, offering tools for security scanning, crawling, and manual testing of web vulnerabilities. Using the right tool for each test scenario is crucial to achieving accurate results and comprehensive coverage. QSS Technosoft combines these automated tools with expert manual testing to deliver deeper insights and robust security assessments.
Challenges in Security Testing
Keeping Up with Evolving Threats
The rapid evolution of cyber threats makes it challenging to keep security testing up to date. Organizations must continuously update their testing methodologies and tools to address new vulnerabilities effectively.
False Positives from Automated Tools
Automated security testing tools often generate false positives, which can overwhelm security teams and delay the identification of real issues. Combining automated scans with expert manual analysis helps reduce these inaccuracies.
Lack of Skilled Cybersecurity Professionals
There is a global shortage of skilled cybersecurity experts, making it difficult for organizations to conduct thorough security testing in the digital age. Investing in training and leveraging managed security services can help bridge this gap.
Testing Without Disrupting Production Systems
Performing security tests without impacting live production environments is a critical challenge. Using isolated testing environments and scheduling tests during low-traffic periods can minimize disruption while ensuring thorough assessments.
Best Practices for Conducting Effective Security Testing
Conducting security testing requires careful planning and execution. Here are some dos and don'ts to keep in mind while going for security testing:
Dos
Establish clear objectives
Clearly define the scope and goals of the security testing. Identify which areas need to be tested, such as network security, application security, or data security.
Conduct regular security assessments
Security testing should not be a one-time activity. Regular assessments should be conducted to ensure that the systems and applications remain secure over time. This helps in identifying new vulnerabilities that may arise due to software updates or changes in the threat landscape. Integrating security testing within the broader scope of software testing ensures that security considerations are addressed throughout the development lifecycle, leading to more robust and secure software products.
Adopt a systematic approach
Follow a structured and systematic approach to security testing. This includes conducting a thorough risk assessment, identifying potential threats and vulnerabilities, and prioritizing them based on their impact and likelihood.
Collaborate with developers
Involve developers throughout the security testing process. This can help in identifying and fixing vulnerabilities early on in the development cycle, saving time and effort.
Simulate real-world attacks
Use realistic attack scenarios to mimic real-world threats. This can help in identifying vulnerabilities that may be missed during traditional testing techniques.
Don'ts
Assume everything is secure
Never assume that the systems and applications are secure just because they have passed previous security tests. New vulnerabilities can emerge at any time, and regular testing is necessary to identify and mitigate them.
Rely solely on automated tools
While automated tools can be helpful in finding common vulnerabilities, they should not be relied upon entirely. Manual testing is essential to uncover complex or unique vulnerabilities that may be missed by automated tools.
Overlook physical security
Security testing should not be limited to just digital aspects. Physical security measures such as access controls, video surveillance, and secure storage should also be considered.
Forget about compliance
Security testing should align with industry regulations and compliance standards. Ensure that the testing process complies with relevant standards such as HIPAA, PCI DSS, or GDPR.
Ignore documentation and reporting
Proper documentation and reporting of security testing activities are essential. This helps in understanding the test results, tracking progress, and communicating findings to stakeholders.
By following these dos and don'ts, organizations can ensure that their systems and applications are thoroughly tested and secure. This proactive approach to security testing can help in preventing potential security breaches, safeguarding sensitive data, and maintaining customer trust.
Read Also: Cutting AWS Costs with IPv6: A Comprehensive Guide to Migrating from IPv4 to IPv6 for Elastic IPs
How QSS Technosoft Helps Secure Your Digital Infrastructure
QSS Technosoft offers comprehensive security testing services designed to protect your organization's digital assets and infrastructure from evolving cyber threats. Our expert team utilizes advanced security tools and methodologies to ensure your systems remain resilient and secure.
Our Service Offerings Include
End-to-End VAPT Services
We provide thorough Vulnerability Assessment and Penetration Testing (VAPT) to identify and remediate security vulnerabilities across your networks, applications, and infrastructure, simulating real-world attack scenarios to strengthen your defenses.
Industry-Specific Compliance Testing
Understanding the unique security requirements of various sectors, we offer tailored compliance testing for industries such as healthcare, fintech, and more, ensuring adherence to regulations like HIPAA, PCI DSS, and GDPR.
Security Audits and Source Code Reviews
Our detailed security audits evaluate your organization's overall security posture, while in-depth source code reviews help detect and fix vulnerabilities early in the software development lifecycle, promoting secure software development practices.
Ongoing Monitoring and Risk Management
We provide continuous monitoring services to detect and respond to emerging threats promptly, helping maintain security and minimize risks over time.
Success Stories
- Assisted a leading healthcare provider in achieving HIPAA compliance through rigorous security testing and remediation, significantly reducing their risk of data breaches.
- Conducted comprehensive penetration testing for a fintech company, uncovering critical vulnerabilities that were promptly addressed, enhancing their security posture and customer trust.
- Performed source code reviews and security audits for a software development firm, enabling them to integrate security into their development process and deliver secure software products.
- Partner with QSS Technosoft to gain the expertise and tools necessary to protect your digital infrastructure effectively in the digital age.
Conclusion
Now you probably know why security testing is important for your business. So, in order to effectively combat the growing cyber threats in the digital age, organizations must prioritize security testing as a fundamental aspect of their security strategy. This not only safeguards confidential information but also helps organizations comply with regulations, build and maintain customer trust, and minimize the financial and reputational repercussions of security incidents.
As an experienced provider of security testing solutions, QSS Technosoft is equipped to assist organizations in identifying and mitigating potential security risks. With our expert team and cutting-edge technologies, we can help organizations develop a robust and resilient security posture.
To secure your organization's digital landscape and ensure your protection against cyber threats, reach out to today for a consultation. Let us help you fortify your defenses and pave the way for a secure and prosperous future.
We are proud to mention that our work has been recognized by leading B2B reviews and research platforms like GoodFirms, Clutch, MirrorView, and many more.
Partner with QSS Technosoft to build a secure digital future.
Contact us today for a customized security testing solution.
FAQs Section
Why is security testing important?
Security testing is crucial because it helps protect sensitive data, prevent data breaches, identify potential vulnerabilities, ensure compliance with regulations, maintain customer trust, and reduce the financial and reputational damage caused by cyber attacks.
What are the common types of security testing?
Common types include vulnerability assessment, penetration testing, security code review, security architecture review, ethical hacking, posture assessment, and security auditing.
What tools are commonly used in security testing?
Popular tools include Metasploit for penetration testing, Nessus for vulnerability scanning, SQLMap for SQL injection testing, MobSF for mobile application security testing, Intruder for cloud vulnerability scanning, and Burp Suite for web application security testing.
How often should security testing be performed?
Security testing should be conducted regularly and continuously throughout the software development lifecycle to identify new vulnerabilities and adapt to evolving cyber threats, including malicious attacks.
What challenges are faced in security testing?
Challenges include keeping up with evolving threats, managing false positives from automated tools, shortage of skilled cybersecurity professionals, conducting tests without disrupting production systems, and effectively responding to security incidents.
How can organizations improve their security testing effectiveness?
Organizations can improve effectiveness by combining automated tools with manual testing, involving security experts, adopting a systematic approach, conducting regular assessments, and integrating security testing early in the development process.
What is the difference between penetration testing and vulnerability scanning?
Vulnerability scanning is an automated process that identifies known security weaknesses, while penetration testing simulates real-world attacks to exploit vulnerabilities and assess the effectiveness of security controls.
How does security testing help with regulatory compliance?
Security testing identifies gaps in security controls that may violate regulations such as GDPR, HIPAA, and PCI DSS, allowing organizations to remediate issues and maintain compliance.
What role do security experts play in security testing?
Security experts conduct manual testing, analyze results, simulate attacks, provide recommendations, and help organizations develop and maintain a strong security posture against cyber threats.
The Importance of Security Testing in Today's Digital Landscape